Digital assets
VIDEOS & Podcasts
Podcast: A roundtable on solving for secure BYOD
Truly Secure BYOD Should Guarantee Privacy (Interview & transcript)
Whitepapers, Reports, Data sheets

| Gartner® Report |
When and How to Allow Mobile BYOD
Complimentary Report
Hypori Halo CAPABILITIES overview
Defense and regulated industries can protect data and preserve user privacy via secure virtual devices. Hypori Halo uses zero-trust architecture, isolation, and virtualization to eliminate data at rest on the physical device and data in transit, reducing the threat and spread of cyber-attacks.
Hypori Halo for CMMC 2.0 Compliance
With cyberattacks on the rise, controlled unclassified information (CUI) among defense-related businesses is increasingly at risk. Hypori’s secure mobility solution helps the Defense Industrial Base address CMMC 2.0 requirements by improving security efforts and reducing risk.
The Tech That will Unlock Cost Savings for Healthcare IT
This whitepaper presents an innovative technical solution that will transform your approach to empowering healthcare workers from their personal mobile devices.
Ebook - zero-trust BYOD using virtualized endpoint devices
A collection of real-world case studies and potential use cases.
Discover Hypori’s virtualized approach to enable zero-trust access from ANY mobile device with no data in transit and no data at rest – with 100% user privacy.
eBook - Truly Secure byod should guarantee privacy
It's been the unsolvable challenge since personal devices were introduced to the workplace: How does one ensure both the device's security and the user's privacy? Jim Cushman of Hypori outlines how to do both - at the edge - and at a lower cost, too.
eliminate the risks of byod with virtualization
Heavy reliance on mobile devices with their inherent security risks creates vulnerabilities for both enterprises and end-user privacy. Reconsider how to access and engage from the edge by using virtualization to eliminate risks associated with BYOD and preserve end-user privacy.
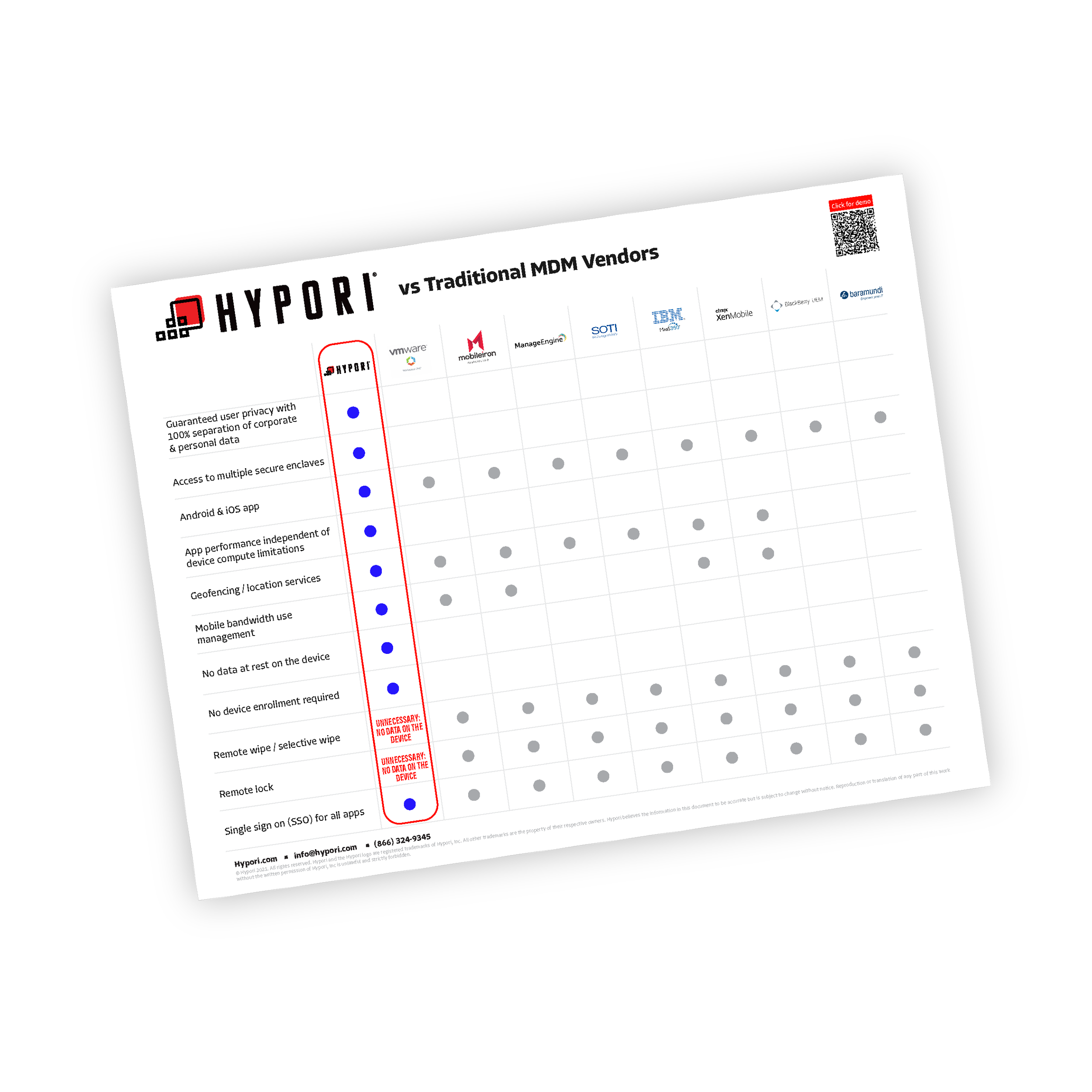
MDM competitive analysis
With cloud-powered apps, zero data at rest, and the ability to access multiple secure enclaves from a single device, Hypori is the clear choice over any UEM / MDM on the market.
See why Hypori is more versatile and secure than traditional MDM.
BYOD Policy Checklist
General checklist to implement a BYOD policy.
Or use Hypori Halo for a simple, more secure, 100% private solution with zero-trust access to enterprise apps and data on any endpoint device.
Multi-Domain Access from a Single Device
Hypori + Garrison’s joint solution enables secure access to additional networks (i.e. NIPRNet, SIPRNet, JWICS) and the internet from a single GFE device.
Discover the benefits of deploying virtual GFE for multi-domain access from a SINGLE device with no data at rest.
Gartner® Report: When and How to allow Mobile BYOD
I&O leaders responsible for end-user computing can use this Gartner® report to determine whether or not they should implement mobile BYOD and, if so, which BYOD variant to select.
On-Demand Webinars
More digital assets
Still have questions? Check out the FAQs.
Source: Gartner, When and How to Allow Mobile BYOD, By Analysts: Rafael Benitez, Tom Cipolla, Pankil Sheth, Katja Ruud, 06 March 2024.
Disclaimer: GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.